The Definitive Guide to Risk Management Enterprise
The Ultimate Guide To Risk Management Enterprise
Table of ContentsThe Main Principles Of Risk Management Enterprise What Does Risk Management Enterprise Do?Risk Management Enterprise Things To Know Before You Buy
Control who can see or edit these components by establishing specific gain access to civil liberties for individual customers, ensuring info safety and customized usability. Enables customers to customize their user interface by choosing and preparing important information components. Supplies an individualized experience by permitting personalization of where and just how data aspects are presented.It enables accessibility to real-time incorporated data immediately. Centers can make use of extensive data knowledge for quicker and much more informed decision-making.

Diligent is a threat monitoring software program that enables maximizing performance, and improves development. It also helps keep an eye on risks with ERM software that includes incorporated analytics and adapts to your business demands.
The Ultimate Guide To Risk Management Enterprise
Simplifies the procedure of gathering threat information from numerous parts of the organization. Gives leadership and the board with real-time threat insights. Usage ACL's innovative analytics to detect danger patterns and predict dangers.
This enables companies to catch danger insights and warnings in the third-party vendor's security report. This enables conserving risk analyses as auditable files. It additionally permits exporting them as PDFs. To complete the procedure companies can complete a reassessment date. Allows business to capture and record threat insights and warnings in third-party supplier safety reports.
It additionally minimizes danger via structured conformity and danger management. It can help accumulate and track all your risks in the Hyperproof risk register.
It provides fast access to essential info and paperwork. This ensures the safety and security of Active proof instances by allowing multi-factor authentication (MFA) using authenticator apps such as Google Authenticator, find out here Microsoft Authenticator, or Authy.
The Single Strategy To Use For Risk Management Enterprise
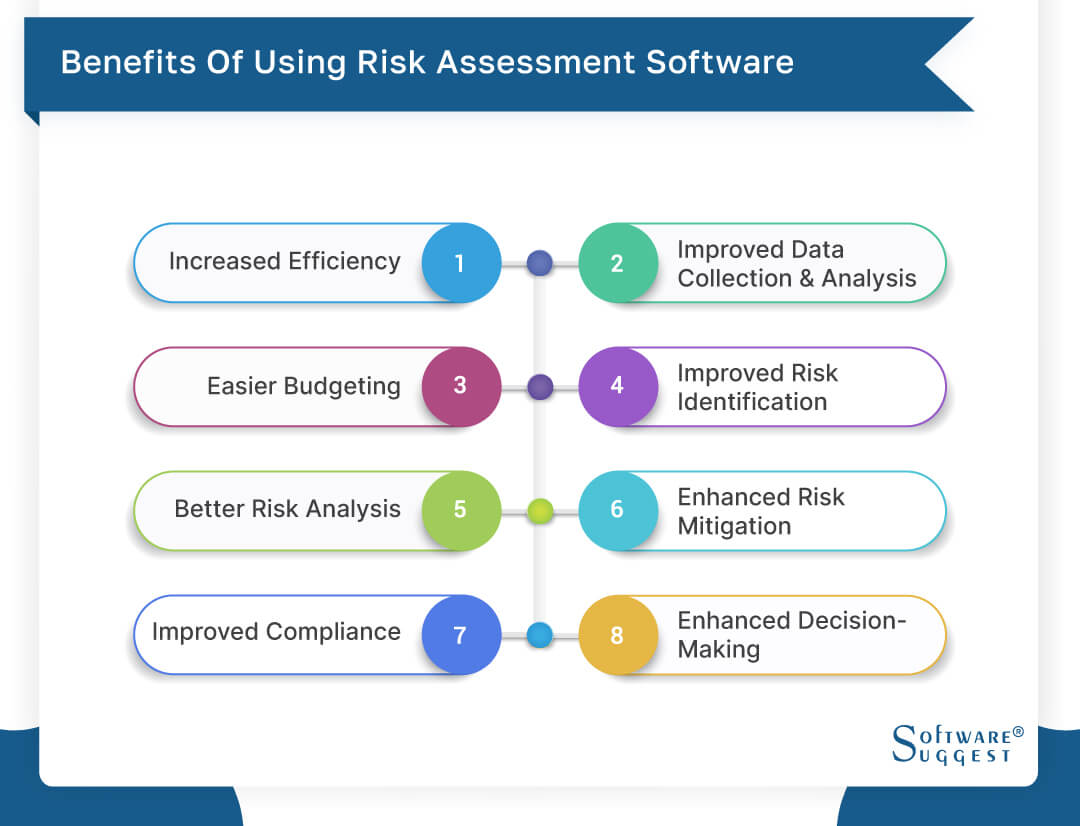
It enables smooth operations and combinations and reduces ineffectiveness. It offers top-tier protection attributes to secure delicate information. This threat management software application is a best device for centers wanting to take care of unneeded concerns or threats. It includes several types of features that make it particular for ERM pop over to this site supervisors. Right here we have highlighted several of its vital functions for your benefit, so have a look.
Individuals can also make use of the AI-powered tools and pre-existing material to produce, evaluate, focus on, and address threats efficiently. reference Improves the procedure of configuring and inhabiting threat signs up.